At present, countries all over the world attach great importance to cultural works. These works have become an important engine of economic development and can make good contributions to economic growth. The traditional tracing control scheme of cultural creation works has some problems, such as incomplete information collection, critical point of unit tracing, information fraud, centralized data storage and so on. At the same time, there seems to be a series of problems that can be solved. This paper analyzes the current situation of the review data of cultural creation products, and puts forward the review and analysis scheme of cultural creation works based on large-scale data algorithm and block chain technology. In addition, by combining department chain technology with intranet and traditional database system, an information database about the supply chain of cultural products in crop departments is established. The processing, logistics and sales information and the information of participants are interrelated.
With the development of economy and diversified culture, the importance of protecting and inheriting special culture in China has been gradually strengthened [1]. Vigorously developing CCP is not only an important means to create characteristic brands and promote regional economic development, but also an important means to maintain and develop China’s rich cultural diversity [2]. Therefore, as designers of cultural creation works, they must strengthen their deep understanding and understanding of the traceability of cultural creation works, and formulate effective schemes for the retrospective utilization of cultural creation works [3].
The relevant personnel must dig deeper and go to the cultural attributes behind the products, carefully screen, confirm and utilize them in the design, and really convey the cultural information that needs to be expressed to the users in time with the help of effective design [4, 5]. In addition, the design of the shape, structure, color scheme and other aspects of the design, but also need to fully consider the use of the way and the actual consumer demand [6].
However, there are many problems with traditional cultural and creative product traceability systems. First of all, traceability data storage is centralized, and traditional cultural and creative product traceability systems are mostly established based on centralized databases (such as MySQL). In traditional cultural and creative product traceability systems, data are stored in trusted central servers, managed and operated by various companies, and participants in the traceability chain each maintain a ledger [7].
Secondly, there is a single traceability point and a lack of unified standards. Scholars conduct relevant research on the construction of traceability systems based on different traceability technologies [8]. These problems need us to use the new technology of the moment to make targeted solutions, and blockchain becomes a good choice [9]. Applying blockchain technology to CCP has the following characteristics;
Decentralization: Traditional data services usually require a centralized entity in which all data is stored and with which we must interact in order to obtain the needed information. Because they are centralized, all data is stored at one point, which makes them an easy potential target for hackers [10]. If the centralized entity is shut down for some reason, we won’t be able to access the information we need. Blockchain technology, on the other hand, has a decentralized nature, where information is not stored by a single entity throughout a decentralized system, but each individual in the blockchain network owns that information [11];
Transparency: Blockchain technology means that anyone can access any information stored on the blockchain, so everyone’s information is open and transparent, and for each participating subject, the trace of each subject on the chain can be traced due to the blockchain technology. It is impossible for any subject to hide some or all of the information by using power or order, and all subjects participate in an equal manner. The information of the whole blockchain can be collected by any participating subject, and the information on the block is accessible to any participating subject without any obstacle;
Invariance: The blockchain adopts a decentralized distributed structure model, and its transaction information data are arranged and combined in a certain order, and the blocks are linked in the whole chain by distance. Once a block is transmitted through many generations, the entire data computation is very large, therefore, the historical data information of a long block is not tamperable.
Some western countries have completed industrialization first and selected developing countries for the development of heavy industries and other industries, and have transferred manufacturing and service industries [12]. With the progress of the times, economic prosperity, and the emergence of diversified market demands, CCP came into being [13]. Traditional culture and future innovation, two seemingly opposing words, are perfectly reflected in CCP [14]. Cultural products without creativity are antiquity, and creative products without culture lack connotation. CCP should use symbolic meaning, humanistic spirit, aesthetic features and other methods to interpret culture, and combine the products themselves to find design points from them, find a balance between tradition and innovation, and finally reconstruct them to vividly interpret traditional culture through modern means, such as bookmarks, mugs, refrigerator stickers and other products launched by the Forbidden City Cultural and Creative, cross-border cooperation with jewelry brands, such a form is popular among the majority of young people This form of cooperation with jewelry brands is very popular among young people, and it deepens the meaning of the concept of traditional culture through modern means, giving new life to traditional culture.
On the one hand, the sale of creative products in tourist areas provides a large number of jobs and promotes the economic development of tourist areas through the economic income of creative products. Creative brands are now sold online through modern means such as the Internet, and creative stores are stationed in major e-commerce platforms. CCP are no longer exclusive to a few audiences, and have expanded their consumer base while riding on the e-commerce express. This enhances the national cultural self-confidence, improves tourists’ sense of participation and experience, and greatly improves the quality of tourism. Finally, the export of Chinese CCP to other countries is also a valuable opportunity to spread China’s excellent culture, which can make countries around the world understand more about Chinese culture, feel the charm of Chinese culture, strengthen cultural exchanges, build China’s cultural image, and strengthen the world influence of Chinese culture [4].
Blockchain was initially applied to the Bitcoin trading system, and the information transfer and value conversion between multiple subjects can be established through block interconnection [15].
Blockchain technology effectively solves the effectiveness and authenticity of data transmission of each node in terms of algorithm and consensus mechanism, improves the drawbacks of traditional IoT traceability, and ensures the authenticity and integrity of information on the chain. Table 1 lists the technical breakthroughs of some IoT + blockchain models in the traceability of CCP.
| Basic links | Terminal Equipment | Technology Breakthrough | Typical representatives |
|
Under the coverage
of Ethernet, through the identification of RFID tags, the entire data of food production, processing, circulation and retailing is sent to the traceability center for chain, which completes the collaborative data record of multiple parties in the food supply chain to achieve origin traceability and cross-border traceability. |
RFID | International Commercial Food on the Chain | Only Chain (VeChain) |
|
Using RFID tags,
each transaction information from production to sales is completely stored in each block in the form of a blockchain ledger, and the blocks are linked by hash values to achieve multi-point simultaneous bookkeeping of multiple subjects. |
RFID | Establishing a fully chained blockchain ledger | Superledger Fabric |
|
Through the built-in
LoRa module terminal, the data of each node is uploaded to the IoT cloud platform through the self-built LAN or WAN, and the open blockchain Lorawan network is realized by using intelligent contract scripts to control the terminal devices and verify the stored data. |
LoRa | Open Blockchain Network | MXC Foundation |
In this paper, we study the traceability supervision scheme of the whole process of CCP based on blockchain technology from production to put into use, develop a traceability framework with supervision, traceability, rapidity, accuracy and security, and realize the supervision and intelligent traceability system quality with multi-nodes and multi-link management.
The traceability system of CCP mainly consists of different layers (see Figure 1), involving seven types of users (see Figure 2).
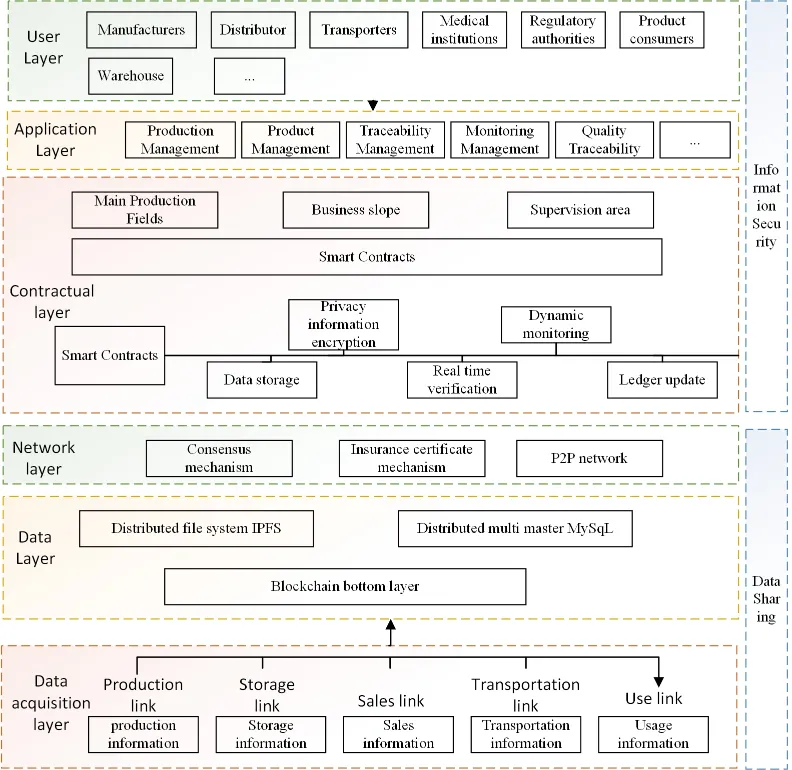
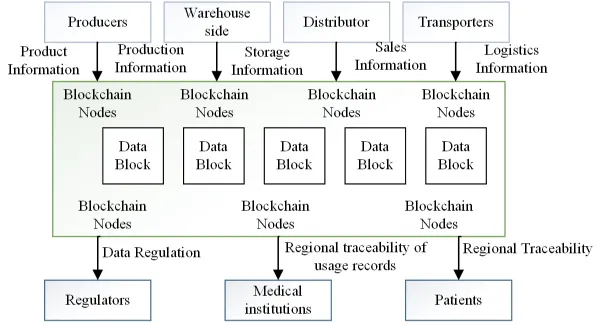
Production link: The main nodes are producers or processors of CCP, which need to enter and upload the product parts information and product information to the blockchain system and create the initial block of the blockchain. In the process, the system automatically carries out data authentication through smart contracts and writes the authentication results into the block together with the product information, while generating traceability codes for the products to facilitate information inquiry by participants of other links.
Storage link: The main node is the warehouse, which stores the products from the production link and writes the link-specific information into the block, and invokes the smart contract to update the changed information to the traceability code when the products circulate to the next link. The process is carried out by consensus algorithm for block broadcasting and information synchronization.
Transportation link: The main node is the logistician. In transportation, it is ensured that each product package contains the identification of this product, and the logistics information of the product needs to be uploaded when updating the information. If the product is broken during transportation (e.g. X-ball tube is broken), the information should be uploaded to the block for the docking management of other links.
Sales link: The main nodes contain distributors and medical institutions. After the transportation link, the product flows to the sellers or medical institutions in different areas, the enterprise information of the current node should be added to the block, and if there is a sale in the next link, the same enterprise information will be added to the block to ensure the integrity of the information.
Use link: This link is mainly designed for the medium and high-end CCP of medical institutions, for example, for the use of large machines such as CT and MRI, information such as replacement of parts or scrapping due to failure during use needs to be recorded on the chain to avoid adverse events caused by improper use.
Inquiry link: Consumers and regulatory authorities, as the main nodes of this link, can scan the QR code of product packaging for product traceability and obtain relevant information; after scanning the code for inquiry, an identity verification will be conducted first, and after passing the verification, the system will conduct block chain address inquiry of the traceability code, and the background will feedback the block information of the address to the front end, which will display it to consumers to realize the CCP The back-end will feedback the block information of the address to the front-end, and the front-end will display it to the consumers to realize the reverse traceability process of CCP.
Recall link: This link is mainly designed for the CCP that generate adverse events. The nodes of medical institutions update the logs of the use of CCP, and the system monitors the logs in real time, and once abnormalities are found, the smart contract embedded in it will be executed, i.e., the recall information will be broadcasted to the relevant nodes immediately, and their contact information will be obtained and the recall notification will be sent automatically.
The data layer stores data from the data collection layer, including collected product information, production information submitted by the producer, logistics and transportation information, and usage information submitted by medical institutions. Off-chain storage service is provided for file data using IPFS, which is a peer-to-peer distributed hypermedia distribution storage system that is better compatible with blockchain. The hash value of file data is saved on the blockchain, and the file data saved on IPFS can be retrieved through the hash algorithm. The secure storage and fast access to file data are realized by using blockchain and IPFS, and other traceability data can be stored to the blockchain and cloud database optionally.
The network includes Fabric-CA, peer nodes, and order nodes, and peer nodes with different functions form their own organizations and exist in different channels (Channels).Gossip protocol is responsible for data transmission between blockchain nodes and synchronization of blockchain ledgers on all nodes in the channel.MSP is responsible for user authentication and determining the communication status of members. The contract layer includes smart contracts for business contracts, data operations, capital turnover, security alerts, etc. Data operation includes the operation of adding and querying data; fund turnover is the automatic execution of operations such as fund flow occurring due to product transactions; security alert is the monitoring of illegal access or bulk operation of data, and an alert message will be sent automatically.
The application layer provides access portal for the user layer by calling the RESTful API designed by the cultural and creative product traceability system to realize user node management, authentication authorization management and management of other operations. Producers, storage parties, transporters, distributors, regulatory authorities, medical institutions and patients are all users of the system. Among them, the manufacturer provides the basic information of the product (including the product’s record registration information) and the parts information, and uniquely identifies the products of CCP with reference to the international standard UDI; the transporter records the circulation information of CCP; the distributor is mainly responsible for the information records of incoming and outgoing goods; and the medical institution is mainly responsible for recording the usage and end-of-life of CCP. Each node on the blockchain has the authority to access relevant data, and the access authority of member nodes of different organizations is different, and their authority is managed by the identity authentication nodes.
The main threat to the traceability system of CCP is the malicious tampering and bulk theft of data by attackers, who may come from outside the blockchain system or from inside the blockchain system. To address the internal vulnerability of the blockchain system, a smart contract with real-time audit and anomaly alarm function is designed to monitor the abnormal behavior of users with identified authorized nodes. The security audit of the traceability system of CCP is realized based on the rules of blockchain traceability information access records, carrying out log analysis and evaluation of data batch reading and writing operations and abnormal use of system resources, sensing abnormalities in a timely manner and issuing early warning reports.
By analyzing the application links and management objects of CCP traceability, the functional modules are divided into three aspects, as shown in Figure 3.
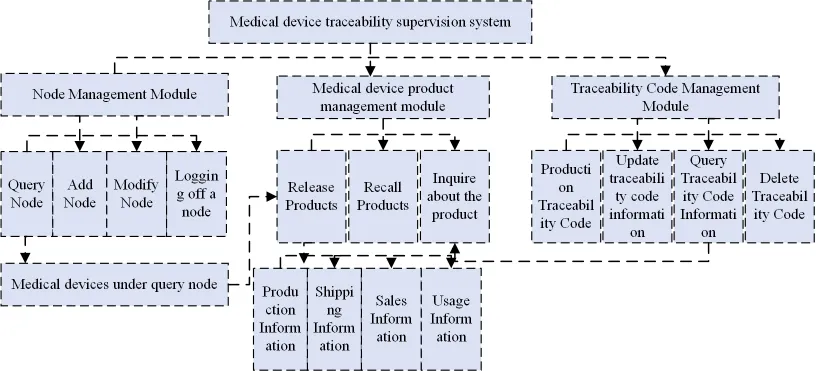
The node management module, i.e. user management module, provides functions including account registration, cancellation, query, authentication authorization and hierarchical management to realize unified login of users and avoid repeated registration of users. Authentication and authorization include CA certificate management and authentication of users, authorization to query and add data, etc.
Only users who are authenticated by the user management module have the authority to add data blocks to the blockchain. This function module can realize the addition of node query results, including the basic information of products. The product management module mainly consists of three aspects: release products, query products and recall products. Released products include production information released by production enterprises, transportation information released by logistics companies, operation information released by sales enterprises, and usage information released by medical institutions. Recall product management i.e. timely recall management of problematic products. Querying products i.e. using the unique traceability code UDI of CCP, the information related to CCP products is read by calling the chain code in the CCP traceability system, and the transaction process on the chain is verified by the endorsement node in the CCP traceability system, and after the order node generates the block, it is deposited to the peer node.
The traceability code management module also includes the operation of deleting traceability codes under specific application scenarios, such as illegal production, and deleting its declared traceability code after banning its production, etc.
To improve the query capability of the system, the CCP traceability system is optimized in terms of data storage and query. The traceability system of CCP involves a large amount of data such as more testing reports, and if these data are uploaded to the blockchain together with other data, it will affect the system throughput rate and concurrency capacity of reverse traceability and reduce the performance of the system, so the multi-party storage model based on ether QL system is adopted, which is implemented as follows.
In the process of storing data, the data are processed in a hierarchical manner according to their importance. Production information and circulation information of CCP are the first necessary data for consumer traceability inquiries, and their correctness should be strictly ensured, so such data are directly stored on the Fabric blockchain. Secondary important information (such as various testing reports, qualification documents, intellectual property rights, etc.) are stored in the cloud with fast access speed and on the IPFS blockchain oriented to file storage. IPFS blockchain technology is mainly oriented to file storage, which can quickly store larger data and the stored data are difficult to be tampered with.
In this paper, we select the specific traceability process of the CCP of a cultural and creative company, which has three types of data flow involving the traceability of CCP, as shown in Figure 4.
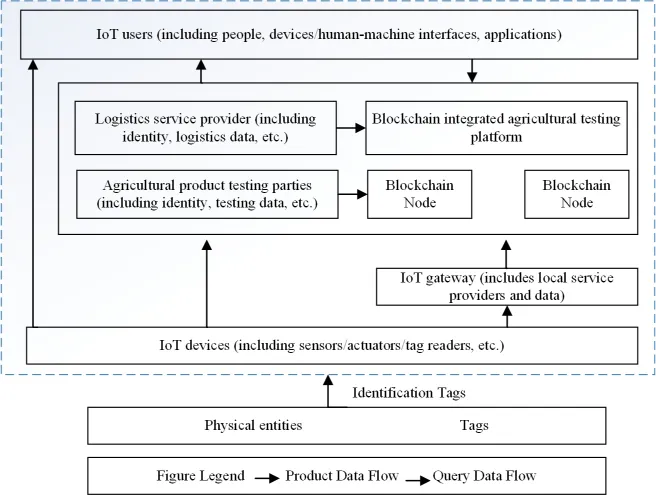
Product lifecycle data flow. Product life-cycle data flow includes data collection and storage of CCP. The IoT sensing devices automatically identify the physical tags, connect the product data to the IoT information transmission system, and transmit the service to the platform service provider through the heterogeneous network, and finally the data flow to each IoT user, in which the data of the whole process of CCP are stored in the monitoring platform of CCP supported by blockchain [17, 18, 19].
Query data flow. The product query data flow includes the three-party query data of relevant enterprises, consumers and regulatory departments, and the data reading open authority of the traceability system is different for different query subjects. The relevant enterprises can inquire about the transaction data information upstream and downstream of the supply chain of CCP; consumers can inquire about the origin, distribution channels and product quality level; the regulatory department is mainly responsible for the effective supervision of product data information in the background, and can realize one-key locking of the same source for problematic CCP, which is convenient for quick recovery.
Identity verification data flow. In the testing platform of CCP, the information of the alliance chain is stored in the multi-center nodes, and the reading and writing of each node member needs to be authorized. The process participants with write permission can use private keys to encrypt and send data related to CCP to complete the information on the chain; regulators and enterprises can use decryption keys to read encrypted information. All the participants of the chain can sign the data of each transaction through private key encryption to ensure the identity of the sender [20, 21, 22, 23], and each transaction information of each node will be recorded in the blockchain ledger. According to the degree of openness, blockchain is divided into three types: public chain, private chain and federated chain, as shown in Table 2.
| Compare Projects | Public Chain | Private Chains | Federated Chains |
|---|---|---|---|
| Degree of Centrality | Decentralized | Centralized | Weakly centralized |
| Participating Nodes | Make anyone | Single Organization | Multiple organizations/enterprises |
| Access mechanism | No need | Required | Required |
| Access rights | No need | Required | Required |
In the experiment, we choose the private chain as the basis for system design, and the flow of data uploading of CCP is shown in Figure 5.
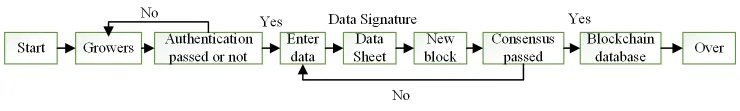
When consumers or government need to query data information of a certain link, the corresponding block is queried by data identification and private key decryption, and the system will retrieve detailed data information from the database and feed back to consumers. The process of querying the data of CCP is shown in Figure 6.
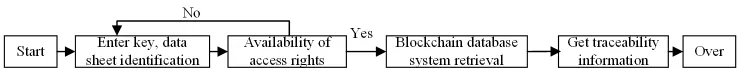
For the traceability blockchain, the block structure is shown in Figure 7.
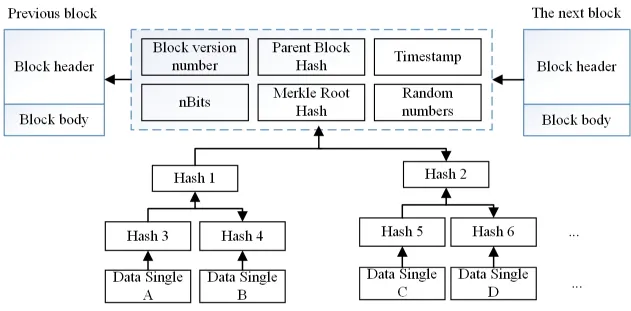
The most critical part of the block is the Markle tree structure. The leaf nodes of the Markle store the hash value of specific traceability information, the non-leaf nodes store the hash value obtained by its child nodes after hash calculation, and the root hash is contained in the head structure of the block. In the cultural and creative product quality traceability scheme, the block stores the index pointing to the data sheet of a certain traceability link rather than the data information itself. At the same time, any change of traceability information in a block will cause changes to the whole Merkle tree structure, and eventually the relevant nodes in the blockchain network will detect the changes and block them, ensuring the immutability of traceability information [24, 25, 26].
| Performance | System 1 | System 2 | System 3 | This article |
|---|---|---|---|---|
| Traceability | ||||
| Integrity | ||||
| Privacy | ||||
| Multi-party storability |
In summary, the huge economic benefits brought by cultural products have prompted them to receive more and more attention. This paper combines blockchain technology with CCP traceability and proposes a blockchain-based CCP traceability supervision system to solve the problems of incomplete information records, data centerization and easy data tampering in the traditional CCP traceability system. The system adopts the underlying technology with finer consensus design at the bottom layer to provide finer-grained access control for the recorded data, thus enhancing privacy protection; the traceability information is uploaded onto the chain and jointly managed by multiple nodes to form a management mode of distributed bookkeeping with multi-link participants; the multi-party storage and asynchronous query mechanisms further enhance the access performance and information security of the blockchain traceability system; the use of smart contracts The system can be managed with smart contracts, security audit and monitoring of malicious attackers. The follow-up work will further research on node role management, improve the management of node roles, and strengthen the privacy protection of information.
This article does not have funding support.
The author declares no conflict of interests.
1970-2025 CP (Manitoba, Canada) unless otherwise stated.