Using blockchain technology to handle the entire chain of digital copyrights in digital libraries not only helps to improve the economy, validity, and fairness of the libraries’ digital resource offerings, but it also increases the revenue of digital copyright subjects in a sustainable manner. In this work, a decentralized, secure, and traceable digital copyright transaction system is designed and implemented using blockchain technology. The system serves creators, administrators, and subscribers through its user layer, business model layer, and Fabric network layer. To guarantee the accuracy and integrity of transaction data, smart contracts are used for the registration of digital works, transaction supervision, and smart contract execution. Fabric Composer is used in the development of the system and offers good scalability. The system still has issues with privacy protection, increasing performance, and complying with laws and regulations. It is anticipated that the digital copyright transaction system will advance in the area of digital copyright protection as blockchain technology develops.
The increasing distribution and sharing of digital works, whilst offering enormous convenience to the diffusion of culture and information, has at the same time sparked an urgent need for digital copyright protection [1]. Conventional digital copyright management systems are frequently run by centralized organizations, making them susceptible to data manipulation and single points of failure. Additionally, these organizations struggle to meet the demands of consumers and authors of digital works for safe and open transactions [2]. Building a digital copyright transaction system with a high level of decentralization, transparency, and security is therefore especially necessary.
Blockchain technology’s novel features make it the perfect solution for issues relating to digital copyright [3]. First off, because it is decentralized, there is no longer a need for conventional centralized management organizations. Additionally, because authors and users engage directly in digital copyright transactions, the complexity of intermediary links is reduced. When digital copyright information is maintained on the blockchain, it is difficult to be deliberately tampered with, offering a strong guarantee for copyright information. Secondly, the distributed ledger mechanism of the blockchain assures data security and tamperability [4]. Furthermore, since each transaction is documented on the blockchain, the traceability of transaction data offers a strong foundation for resolving disputes. Because of this, the digital copyright transaction system that this study built has a well-defined hierarchical structure. The user layer, which is separated into three user categories—creators, administrators, and subscribers—offers service interfaces for managing users and copyright [5, 6, 7]. By using smart contracts to specify the data structure and operational features of the digital copyright trading system, the business model layer ensures the security and openness of the trading data.By building a decentralized communication network by connecting the middle layer and the underlying layer via the Connection Profile file, the Fabric network layer acts as the foundational infrastructure. The construction of business models and the generation of interfaces are finished by Fabric Composer and composer-rest-server, through which users can accomplish the operations of digital copyright registration, transfer and subscription. Because every user action would be documented on the blockchain, the transaction will be traceable and secure [7, 8].
Though it has advanced significantly in many areas, the digital copyright trading system outlined in this study still confronts a number of difficulties. First off, protecting user privacy while maintaining transparency has always been a challenging topic in the realm of digital copyright protection, and more research is needed in this area [9]. Second, there is still concern about the system’s performance scalability, as more users and transactions could put a strain on the system’s capacity. Lastly, another urgent concern for the digital copyright trading system is the enforcement of laws and regulations. More thorough study is needed to determine how to integrate blockchain technology with existing legal frameworks to guarantee the system’s compliance and legitimacy.
All things considered, this paper’s blockchain-based digital copyright trading system offers a novel concept and remedy for digital copyright protection. Nonetheless, given the ongoing advancements in both technology and society, interdisciplinary research and multipronged approaches are still necessary to solve digital copyright issues. The digital copyright trading system based on blockchain is anticipated to become more significant in the field of digital cultural communication in the near future [10, 11].
A blockchain-based digital copyright protection system is one that is built on the blockchain network and offers the benefits of decentralization, safe digital content storage, transaction record traceability, and tamper-proofing [12]. As a result, the new blockchain-based digital copyright transaction system that this study builds is depicted in Figure 1 along with its general architecture.
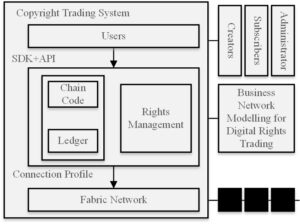
As shown in Figure 1 that the system is roughly separated into three layers based on the types of functions. The user layer, which is the top layer, is in charge of providing interfaces for user and copyright management services. Examples of these include user registration, login management, key management, personal information modification, and copyright registration, query, transaction, and deregistration interfaces.
The middle layer of digital copyright trading is the business model layer, which is created and implemented by the developers. In this layer, the account book keeps track of every user transaction, and the chain code, also known as a smart contract, specifies the data structure and functional features of the system. To accomplish the relevant business functions, users in the user layer use API+SDK to call the chain code in the business model [13]. The copyrighted transaction information may be tracked down the chain since every transaction is documented in the ledger. This paper’s business model can be installed on the nodes of various users more easily with the help of the Connection Profile, which connects the middle layer and the lowest layer, the Fabric network layer. This creates a decentralized communication network by defining the node information and communication ports.
The users targeted by this system are basically divided into 3 sorts of users: creators, administrators and subscribers.
The original author of the digital product, or creator. In order to manipulate the chain code, deposit the details of the digital work (name, DCI, author, type, and creation time) on the blockchain, and change the DCI through the function interface, he can fill out the form with the DCI code of the digital copyright he applied for. He can also call the SDK and remote API provided by Fabric [14].
Administrators, or the authoritative management group, have the ability to oversee the accounts of subscribers and creators while also publishing new contracts to the chain and removing outdated ones.
The subscriber, who is the most frequent user of the public, has the ability to subscribe to a particular digital work on the chain. Upon calling the remote API and executing the subscription chain code, the subscriber gains the ability to read the digital work on the chain.
Contract code, also known as chaincode, is a technical term used in Hyperledger that is used to implement the system’s core logic. During the system’s first phase, the administrators deploy chaincode to the nodes. The user activates the chain code by logging into the client program and utilizing the remote API functions made available by the business model, after the chain code has been successfully configured, instantiated, and installed on the nodes in these three stages. Every node has a client software installed. Each chain code call log, user addition and deletion transaction records, copyright transfer transaction records, work subscription transaction records, and so forth are all kept in the ledger. The ledger is maintained through the process of keeping these transaction records up to date.
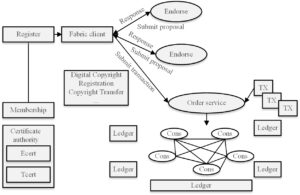
To introduce the transaction procedure of this system, consider publishing a copyright transfer transaction as an example in the following.
After logging in and confirming their identity, the creator of a digital work receives an enrollment certificate (Ecert) and a transaction certificate (Tcert). Subsequently, the user can use the client to initiate a transaction [15].
After logging onto the client successfully, the user drafts a proposal for copyright transfer and distributes it to every endorsing node.
The proposal outcome is sent to the client by the endorsing nodes when they have completed the copyright transfer chain code.
The client gets enough endorsement support and transmits the transaction to the sorting node, which includes the proposal outcome.
A block containing the sequenced transaction is created by the sequencing node and forwarded to every validation node.
Before a transaction is dropped, the validation node constantly conducts a last examination of the transaction from the sorted transaction block structure (including the transaction message structure, signature integrity, whether it is duplicated or not, whether the read and write collection versions match or not, etc.). Following the check, it completes the legal transaction and enters the outcome into the ledger. In addition, it creates a new block, modifies the metadata block within the block, and logs details like the transaction’s legality.
The procedure described above is comparable to publishing copyright subscription transactions, and it won’t be duplicated here. The system’s functions and architecture are covered in great length above. The blockchain-based digital copyright trading system provides the following benefits over traditional copyright management systems:
The blockchain allows authors to preserve their digital copyright data, safeguarding their ownership of their creative creations;
In order to reap financial rewards, creators can assign the copyright to their digital works to other users based on their own pricing. This is accomplished by invoking the copyright transfer chain code on the blockchain, which is transparent and observable throughout the entire fabric network. There won’t be any disagreement over the copyright transfer because the digital works’ copyright is transferred by invoking the copyright transfer chain code on the blockchain, which is visible and observable across the entire Fabric network [16];
Offer a subscription interface for digital works on the chain, allowing regular users to obtain the right to read the digital works by paying a nominal charge to the original creator.
The three modules of the digital copyright trading system-user, asset, and transaction-are covered in this section’s business model as shown in Figure 2.
Users are divided into three categories: creators, administrators, and normal users (i.e., the original proprietors of digital assets) [17]. User=Uid, userName, email, bal-ance, PK, SK, bookList, Admin=Uid, user Name, email, PK, SK, Author=Uid, userName, email, PK, SK, my BookList are the respective tuples that display their attribute structure design. Describe Person is the user base class; regular users, admin users, and creators are in the User category; PK and SK are the user’s public and private keys; balance is the user’s wallet balance; bookList and myBookList record all of the book information that the user has created or subscribed to. The digital copyright transaction is signed using the private key, which guarantees the accuracy and consistency of the transaction data in the copyright transaction [18]. The creator’s balance will rise and the consumer’s balance will fall when these two transactions occur because, as was previously established, the creator of a digital work might profit financially by transferring the copyright or making the work available.
The digital copyright work is the system’s asset, and the following tuple represents its attribute structure. Book= dci, name, category, createTime, description, content, owner, price, subscribePrice, subscribers , DigitalWork =dci, name, category, createTime, description, content, owner The digital work’s unique identifier is called dci; the name of the digitally copyrighted work is called name; the work’s classification is called category; the creation time is called createTime; a brief description of the work is called description; content is part of content information; the owner is identified as the owner of the work; the price is identified as the copyright transfer price; and the subscription price is called subscribePrice. The cost of subscribing to the work is called subscribePrice, and the group of all users who have done so is called subscribers.
In the blockchain system, each invocation of a smart contract (or chain code) by a user is called a transaction [19]. By contacting the function interface supplied by composer-rest-serve, the user can invoke the contract and carry out the necessary actions. in Algorithms 1,2 and 3 display the primary codes for copyright registration, copyright transfer, and digital content subscription transactions.
Algorithm 1 Main code for Copyright Registration
Algorithm 2 Primary Copyright Transfer code
Algorithm 3 Digital Contet Subscription Main Code
We leverage IBM’s fabric1.0 federation chain project as the development platform and create our own digital copyright protection system to give select users the ability to manage users and edit data. According to the node deployment plan given by the official fabric, install docker and docker compose tool on each node, download the corresponding docker image and fabric source code, compile and generate Cryptogen program, and generate public and private keys and certificates with this program and the relevant crypto-conFigureyaml configuration file.
Two types of certificates are generated here: a user certificate issued by the CA for user login and permission control, and a TLS certificate ready for secure communication between nodes. The Genesis block and the Channel configuration block are then generated using configtxgen. After setting up the necessary files, the fabric container may be used to construct the channel, add peer nodes one at a time, and update the anchor node [20]. The fabric network is prepared in this way. The business chain code should then be installed into the fabric network.
The business model of the system is constructed using fabric composer, and the fabric chaincode supports both JavaScript and Golang. This increases the program’s scalability. Afterwards, remote interfaces for the business model can be created using composer-rest-server, and users can access transaction records, digital copyright records, and other data via these function interfaces. When a user provides asset registration data, other nodes package the transaction record into blocks and record it on the chain. Afterwards, the transaction record is unchangeable once it is there.
3. A timestamp-based digital copyright registration system is developed. The fundamental element of distributed storage technology is the timestamp, which is essentially a perfectly verifiable string of letters that indicates the precise time node at which a data state changes. Digital libraries with conditions in China should construct a digital copyright registration system based on timestamps to guarantee that digital copyright information realizes real-time display query, using the Tsinghua University Digital Library’s practice of creating digital resources copyright registration database as a model [21]. First, offer a timestamp-based digital copyright confirmation service. For instance, it can work with established blockchain copyright registration platforms like “Huaxin Valley” and “Copyright Home” to provide the digital copyright registration service of “release as deposit,” issue copyright registration certificates with timestamps, and upload digital copyright registration data to the blockchain in real time. A “release-as-deposit” digital copyright registration service is provided by uploading the registration data in real time to the blockchain [22, 23]. Second, to ensure the information security of digital copyright registration, the timestamp traceability function is employed. The “timestamp + dynamic hyperlink” strategy can be used to stop unauthorized access to digital copyright registration information. Digital libraries can track down the source of copyright registration information tampering in real time by using the digital copyright registration platform and dynamic hyperlinks to store and monitor the information marked with timestamps [24].
On the other hand, P2P peer-to-peer network facilitates fair and transparent trades of digital copyright subjects [25].Distributed storage system is based on a peer-to-peer (P2P) network architecture that performs data transaction publicizing, network routing, and mining [26]. P2P networks can be used by digital libraries to support the relative equivalency of their copyright revenue and infringement liability, as well as to reinforce the contractual nature of digital copyright management [27]. First, a peer-to-peer digital copyright transaction mode based on P2P transmission links was established. In the event that the digital library’s resource retrieval system is converted into a P2P network, the embassy can use the P2P Super Ledger to establish the subject of digital copyright infringement responsibility for the first time and calculate the loss of copyright revenue using the P2P rights and interests proof code. The establishment of a knowledge payment system built on a P2P network is the second. For instance, the main interface of the digital library resource retrieval system has an integrated knowledge payment module that directs users to use this module to access value-added services for digital copyright resources. The P2P network will instantly cut off the proliferation channels of digital resources in the event that the library disobeys legal regulations by disseminating unregistered digital materials.
Employing the data encryption feature of smart contracts to firmly stop digital copyright theft The Tsinghua University Digital Library constructs the firewall of smart social services and makes sure that the digital copyright flow path is always supervised by smart contracts by using two primary data encryption algorithms in smart contracts: asymmetric encryption and cryptographic desensitization. Digital libraries should therefore make use of smart contracts’ data encryption feature to safeguard the confidentiality and integrity of digital copyrights. Asymmetric encryption technology is first utilized to strengthen digital copyright defenses against forgery assaults [28]. Both public and private key encryption are available for use by digital libraries to manage digital copyrights: public key encryption can be used to add digital watermarks to copyrights with low security levels, enforce identity verification and access control, and lower the risk of malicious copyright forgeries; private key encryption can be used to grant the copyright owner the ability to independently set up copyright invocation methods and to completely prevent the use of phishing to steal copyright information [6, 7]. Second, the security of digital copyright invocation is improved by the application of encryption and desensitization technologies. The Tsinghua University Digital Library’s digital copyright data contextualization desensitization scheme is one example that can be cited. It uses encryption and desensitization techniques like invalidation, random value replacement, data replacement, offset and rounding, among others, to counteract hacker attacks in intelligent social services and converts the frequently accessed digital copyright information database into an encryption and desensitization scheme [16].
This work was supported by Soft Science Project of Weifang Science and Technology Bureau: Information Construction of Scientific Research Files in Local Universities under the Cloud Computing platform (No.: 2022RKX038).
The authors declare no conflict of interests.