As a product of the revolutionary war years, red culture, with its strong vitality, strong cohesion and extraordinary charm, with its incomparable positive energy, resists vulgar and flattering culture, promotes people to rebuild their faith, purify their minds, stimulate their motivation, and promote the process of cultural power. Yan’an, represented by red culture, is rich in resources. This is the holy land of Chinese revolution, the first batch of famous historical and cultural cities named by the State Council, and the three major education bases of patriotism, revolutionary tradition, and Yan’an spirit. The development and utilization of such resources have great political, cultural, educational and economic values. This research is based on the development of red culture, and uses the distributed machine learning system to realize in the system architecture of parameter server. In the distributed system set in this study, node downtime and network interruption are random. When the parameter server system adopts static scheduling, it leads to poor scalability and robustness. The experimental results show that under the intelligent simulation of machine learning system, the development of red culture resources meets the expected assumptions, and the accuracy of the model is relatively high.
In Chinese traditional culture, “red” has the meaning of “auspiciousness, jubilation and success”, and “red” began to be closely linked with the revolution with the outbreak of the French Revolution in the 18th century [1]. After the October Revolution, Russia formed the “Red Army” and established the “Red Zone”, which gradually became the symbol of “socialism” and “communism”. In the period of the Chinese revolution, “red” is still a synonym for revolutionary and progressive forces [2]. It represents the “red revolution” and “red regime”, is the birthmark of the CPC, and is opposed to the white terrorist regime led by the Kuomintang. Red cultural resources are a part of cultural resources and a special kind of cultural resources. At present, there are three main views on the definition of cultural resources in the academic circle. This definition fails to highlight the difference between culture and culture as a resource, which is too wide to highlight the particularity of cultural resources [3,4]. The second is the theory of cultural materials, which points out that cultural resources are various materials with cultural attributes. The third is the theory of cultural elements, which points out that cultural resources are various cultural elements developed and utilized by human beings in various activities [5].
Whether the red cultural can be deeply developed will be considered to a great extent.Think political education red culture resources development subject’s idea, quality and ability influence, because it is the whole.The leader and main executor in the process of resource development. It plays the role of connecting link and communication bridge between the content and the object of education [6,7]. This requires ideological politics.The development subject of educational red cultural resources should set up scientific development idea and strengthen the cultivation of development quality. Promote the construction of their own development capacity [8,9].
Red cultural resources are the cultural resources congealed by the blood and sweat of countless revolutionary ancestors [10].With a strong and brave patriotic feeling and dedication, not for the people feelings, and constantly explore and create.The new and innovative spirit keeping pace with The Times, these are the spirit of ideological and political education to be developed and constantly developing [11].Motivation and valuable wealth. Under such a premise, we should adhere to the combination of inheritance tradition and development and innovation.To realize the innovation and deep development of the red cultural resources. Finally adhere to inherit the excellent tradition, in the process of inheritance development [12]. Because inheritance and development are the process of cultural innovation.In the two aspects, it is time to inherit the excellent tradition in the red cultural resources of ideological and political education.
In recent years, different disciplines have conducted in-depth research on digital technology from different perspectives and levels. At present, digital technology is being used in many disciplines. Which brings greater technical challenges while enjoying convenience [13,14]. Digital technology refers to the use of high-tech equipment (cameras, scanners, computers, etc.) to convert and process the digital images and models of objects’ entities, text materials and other related information.
A distributed machine learning system usually includes synchronization, communication, training, scheduling, data storage and other modules, often considering the special requirements of the system for robustness and algorithm accuracy [15].
To sum up, red cultural resources have a profound historical background and rich spiritual connotation. They have the value and function of cohering the hearts of the times, stimulating the public emotions, and highlighting the spirit of the times. They are an important cultural support for a harmonious society and adapt to the cultural needs of building a socialist harmonious society.
Adoption of the LPIPS metric for evaluating the quality of generated cloud-free images, focusing on perceptual similarity to better match human visual perception.
One of the core issues is empirical risk minimization. As shown in Eq. (1).
The development object, and the development method, which constitute the logical system of “who develops what develops how to develop” [16]. One method that can be used to deploy distributed machine learning applications is to use existing mature general distributed computing frameworks such as MapReduce and Spark. The basic process of MapReduce is shown in Figure 1.
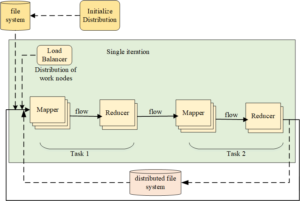
The new machine learning distributed system is a parameter server architecture. The parameters mentioned here refer to key value pairs (keys, values) used to describe model parameters in machine learning, or two-dimensional matrices, or multidimensional matrices. At the same time, multidimensional matrices are also called tensors. Figure 2 shows the architecture of a typical parameter server.
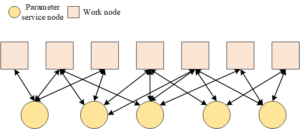
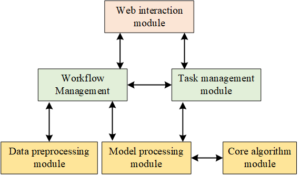
Therefore, it is an unbiased estimate to calculate the gradient with all data by using the method of putting back the training set data, which also guarantees the correctness of the random gradient descent theory. The overall framework of the system has been introduced in the previous chapter, Figure 3 shows the role of modules in each layer of the system logic structure has been described.
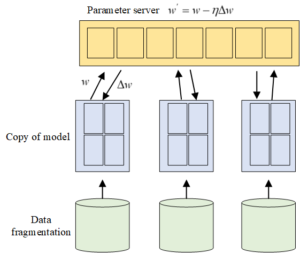
First, digital technology has now entered a variety of disciplines, and has achieved good results. It has accelerated people’s work efficiency. The file management and information management of college students all reflect the rapidity and timeliness of digital technology [17]. If we can effectively combine digital protection technology and apply it to the protection of red cultural resources, we will vigorously save some dying martial arts, make it reappear and recover, and show it in the public’s view more widely. Divide the data set, process different data subsets for each model replica, and periodically perform interactive merging of each model replica. As shown in Figure 4, data is divided, and global parameters are maintained by all service nodes.
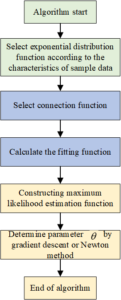
First, select the corresponding distribution function according to the characteristics of the data to be regressed or classified, for example, select the Gaussian distribution for the continuous data, then establish the relationship between the linear prediction quantity and the prediction variable by constructing the connection function to obtain the fitting function, then construct the maximum likelihood function, and use the gradient descent method or Newton method to solve the parameters. If the model is successfully constructed, the test data can be regressed or classified by fitting function, as is shown in Figure 5.
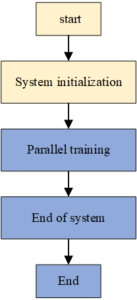
With the arrival of the digital era, digital protection is a new type of channel for protecting information and data generated by modern equipment and technology, including computer technology, 3D technology, photography technology, etc. It collects all kinds of information and materials, converts them into digital and storable information through computer electronic processing, and can share them on the network to achieve real-time interactive sharing. The whole workflow of distributed machine learning system includes system initialization, parallel training of models, and system completion, as is shown in Figure 6.
There are many red cultural resources with a rich variety and far-reaching influence in various parts of China, among which “the red education base is the main position to carry spiritual and cultural resources and spread red culture”.
For different types of cultural resources, the digital protection means are also different, but the digital mechanism used is the same, which is based on 0 and 1 binary digital technology. However, when it comes to each digital technology, the digital technology used, and its final role are not single. For example, the formation of database construction cannot be separated from the early digital acquisition technology; The functions of the database after completion are not single. In addition to the digital storage function, it also includes the digital display function. Therefore, it needs to rely on other digital technologies to play a role together.
To sum up, compared with the material cultural heritage, there are only a few examples of the application of digital technology in red cultural resources, and the two have not been well combined. More technologies are mainly used with low complexity.
By summarizing common distributed and parallel machine learning algorithms, these algorithms are roughly classified according to communication mode and aggregation mode. The communication methods are mainly divided into synchronous and asynchronous. The asynchronous communication uses shared memory and locks to ensure the correctness of the model update. However, single machine optimization and hardware upgrade have limited improvement on training performance. With the development of distributed technology, parallel training model has become a new research direction. Table 1 shows some common distributed and parallel machine learning algorithms and their characteristics.
| Algorithm name | Single machine optimization | Parallel mode | Communication mode | Aggregation mode |
| Synchronize SGD | SGD | data | Synchronization | Gradient summation |
| ADMM | unlimited | data | Synchronization | Add all models |
| EASGD | SGD | data | Synchronous/asynchronous | Add all models |
| Asynchronous SGD | SGD | data | asynchronous | Add all models |
| Adadelay | SGD | data | asynchronous | Partial model addition |
| Hogwild | SGD | data | Asynchronous lock free | Add all models |
Distributed machine learning uses parallel training of multiple nodes within or across the cluster to accelerate training through cooperation between working nodes. Communication is an essential link to achieve node cooperation. However, the network state and network transmission speed in distributed systems are often limited, and communication will become the bottleneck of distributed machine learning. In the core algorithm module, the algorithm model is the core data structure. The query or scheduling of the algorithm model in the workflow management module and task management module will involve the model structure of the algorithm. Therefore, the algorithm model table is the most important one of the several basic tables of the system operation, and its structure is shown in Table 2.
| Field Name | Field Type | Field Description |
| model_ id | varchar | Model ID, primary key |
| parameters | varchar | Parameter table id of training model |
| algo_ id | int | Identification of algorithm, representing the algorithm type corresponding to the training model |
| algo_ name | varchar | Algorithm name of training model |
| data_ frame | varchar | Training data frame ID of training model |
| description | varchar | Model description |
| status | int | Model status, training not started, training in progress or training completed |
Resource development cannot be separated from protection. Protection is the premise of development, and development is for better protection. We should actively strive for the support of policies, funds and projects in the central and provincial levels, set up special funds and special institutions and professional teams in local finance, spare no effort to protect the red cultural resources in Yan’an, promote the development in the protection, and scientific red cultural resources in Yan’an. For some application data messages, the scale of the application data is very large. When there is only one message sending daemon thread, it is easy to cause the message sending to take too long, resulting in the long waiting time for other system messages with short data size. Therefore, when sending a long message, the runtime system automatically splits the long message and maintains the sending status of each segment of a long message to ensure that the data receiver can correctly combine the messages, as shown in Table 3.
| Abbreviation of message usage type | Description of the purpose of the message | Message initiator/receiver role |
| REGISTER_ NODE | The logical node reports to the master node | Three logical nodes of the system |
| NODE_ INFO_ LIST | Node topology information | Three logical nodes of the system |
| NODE_ INFO_ ACK | Node topology information receipt information | Three logical nodes of the system |
| SYSTEM_ READY | System initialization completion information | Three logical nodes of the system |
| TENSOR_ PARTITION | Tensor partition information | Three logical nodes of the system |
| JOB_ DONE | System end information | Three logical nodes of the system |
| PULL_ TENSOR | Pull parameter information | Tensor management module |
| UPDATE_ TENSOR | Update parameter information | Tensor management module |
| ACQUIRE_ KEYS | Task scheduling information | Dispatching management module |
| ENGINE_ STATISTICS | Parameter Service node load information | Dispatching management module |
| ENGINE_ BARRIER_ WAIT | Phase group synchronization information | Stage management module |
| ENGINE_ CONTINUE | Phase group synchronization cancellation information | Stage management module |
Adhere to the principle of coordinated development of red culture and superior resources. In addition to the red cultural resources that attract the attention of giants, papercut, Yangge in northern Shaanxi. The development of red cultural resources must be coordinated with historical culture, folk culture, ecological civilization, etc., and comprehensively developed to maximize social and economic benefits. V in Table 4 represents the size of vocabulary, that is, the number of words in all different texts; L stands for the number of all words. The words here generally refer to strings that are not separated by blank characters; The L/D band represents the average length of the text.
| Dataset | V | L | D | L/V | L/D |
|---|---|---|---|---|---|
| Common Crawl | 673497 | 1147291316 | 2773795 | 1704 | 415 |
| NYTimes | 10637 | 99542126 | 299753 | 979 | 333 |
| PubMed | 141044 | 737869084 | 8200000 | 5232 | 90 |
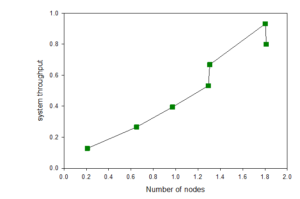
The development of the red cultural resources of political education needs to extract the same ideological policy from the massive red cultural resources.To manage the material and spiritual and cultural resources corresponding to education, but the current integration of these resources is insufficient.The utilization rate of red cultural resources of ideological and political education in material form is low. To the challengeIt is also proved that system can be deployed on multiple general-purpose computers to solve machine learning applications with larger data scale, as is shown in Figure 7
The selection and optimization parameters are extremely important. The design of algorithm parameter table can reflect the expansion ability of the algorithm. Table 5 is the database table structure of K-means algorithm parameters. Users need to read and write the database when querying the algorithm model or setting parameters.
| Field Name | Field Type | Field Description |
|---|---|---|
| model_ id | varchar | Unique model ID of parameter configuration |
| training_ frame | varchar | ID of training data frame |
| validation_ frame | varchar | The ID of the evaluation data frame |
| k | int | Expected number of clusters |
| init_ mode | enum | Selection method of initial clustering center |
| kfolds | int | K fold cross check |
| max_ iterations | int | Maximum training iterations |
| seed | bigint | Random seed during cluster initialization |
| max_ runtime_ secs | double | Maximum running time allowed for model training, 0 is off |
| epsilon | double | Threshold of algorithm iteration convergence |
In recent years, with the rise of red culture research, many scholars began to devote themselves to the red culture resources.Into the ideological and political education, to explore the relationship and fit between the two, which also makes the red cultural resources.The value of ideological and political education is more and more prominent, but it also appears in the development of red cultural resources.Some problems and deficiencies, and the emergence of these problems for the discussion of ideological and political education red cultural resources open.Hair has certain reference significance. Therefore, the author from the analysis of ideological and political education red culture resources development main.Body, object and method of the existence of the error, find the reason for the existence of error, and then to systematize clear solution.To provide the basis for the thinking of the problem.
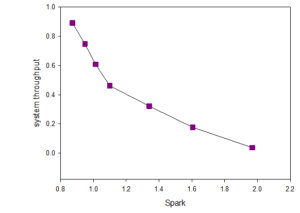
The performance test of the system is mainly conducted by comparing with the Mahout of Hadoop cluster, using the same training data set for the same algorithm model training,. Based on the number of different computing nodes, different computing platforms cluster the same dataset, as is shown in Figure 8.
To sum up, scattered and potential red cultural resources through the main body, achieve of red culture education, and further promote the transformation of China’s red cultural resource advantages into the educational advantages of ideological and political education.
Development resources ideological political education, excavated has research value significance. At the same time, it is also a long-term and complex research project. Although there are relatively many research on red culture, red cultural resources, ideological and political education resources, etc., we can draw a conclusion that it is necessary to protect red cultural resources digitally, and from the internal conditions, external conditions, and presentation results, we can draw a conclusion that it is feasible to protect red cultural resources digitally. However, the reality is not satisfactory, not only is the application of digital technology low. Only by solving these problems, can digital technology better serve. The suggestions put forward in this paper are general. What specific digital technology and what specific solution should be adopted in actual work need to be analyzed according to the situation. Better digital technology needs to be explored and better solutions need to be considered. Only through continuous research can red cultural resources and digital technology be better combined, and intangible cultural heritage digital protection work can be better carried out.
This study was supported by the following funds:
Humanities and Social Sciences Research Project of the Ministry of Education, Research on Traditional Chinese Needlework Artistic Aesthetics and the Spirit of the Times, Project number: 22YJA760031.
2021 Special Project on Educational Teaching Reform in Central Universities, the Beauty of Intangible Cultural Heritage Art (The Core General Course of Wuhan University).
1970-2025 CP (Manitoba, Canada) unless otherwise stated.