The core of financial institutions’ big data lies in risk control, making network security threat identification essential for enhancing data processing and service levels. This study applies the principles of network information transmission security prevention, combining frequency domain analysis and distributed processing to extract threat characteristics. A financial network security threat identification model is developed using BiGRU and Transformer models, and a SQLIA defense system is constructed by integrating multi-variant execution and SQL injection attack prevention. Additionally, an intelligent network security defense strategy is formulated based on finite rationality theory. Simulation results show an F1 composite score of 90.78% for threat identification, and the STRIPS-BR defense strategy reduces relative risk by 74.81% during peak times compared to other strategies. Supported by big data, this system ensures secure data transmission and enhances the network service capabilities of financial institutions.
In the context of big data, the occurrence of financial risks is closely related to financial information, and the improper use of financial users’ personal information can cause many problems. Finance is the core of the modern economy, the financial market is the artery of the whole market economic system, for financial institutions and the financial industry, the degree of security of financial information is closely related to the dilemma. Financial information security dilemma is the result of large-scale accumulation of risk, which is the extreme caused by financial information insecurity [24,1,11,29].
Big data finance refers to financial services utilizing big data technology, which can promote financial institutions to launch new financial products and financial services, deeply mine financial users’ personal information and private data, and provide means for financial institutions to carry out financial innovation and develop high-value commodities [7,8,20,16]. However, with the continuous development of social economy, big data finance has also triggered new security dilemmas while providing convenience for people’s daily life. Financial institutions recklessly collect, store, and use user data information, leading to a sharp rise in the risk of telecommunication fraud and account theft [14,9,22,2]. In response to issues such as the risk of financial information security in the big data environment, users often generally lack sufficient awareness. And due to the users’ neglect of the value of financial information itself, they may further ignore the privacy risks that may arise in the process of financial information management, especially based on the use of big data technology [27,6,19,21]. Therefore, it is very necessary to rationally reveal and clearly analyze the financial information security problems, provide corresponding countermeasures and reflections and build an information security system [28].
Literature [3] emphasizes that the development of technology has created opportunities and challenges for the financial sector, which is currently facing cyber threats such as data breaches. The props used by the group of cyber attacks were studied to reveal the basic framework of cyber attacks and the impact it has on financial institutions. Literature [25] states that an important factor to consider in using big data is privacy security. The possible security issues are discussed using a banking institution that has adopted the BeiDou system as a case study, and the results of the experiment are complementary to the current research areas of big data and information security, in addition to being able to provide a reference for the development of security strategies for enterprises in the big data environment. Literature [23] designed a series of interview questions with Canadian cybersecurity professionals in the context of financial institutions facing significant security risks. The results of the interviews confirmed the potential threat posed by cyberattacks to the financial sector, and the researchers made policy recommendations accordingly. Literature [10] suggests that protecting data without being compromised is important in the cyber age, and the use of machine learning, biometrics, and data learning can prevent data from being compromised. For banks, methods such as biometrics and digital signatures can ensure the security of transactions and reduce threats to the banking system. Literature [18] indicates that the increasing reliance on artificial intelligence to process financial data has led to rising data security issues. Research has shown that the application of AI in big data management can effectively improve the security and privacy of AI in the financial industry, while at the same time increasing the attacks from complex networks. Literature [17] states that financial data protection has become a very important issue in the context of technological development. The challenges to cyber security and the effectiveness of existing protection measures were analyzed. The results show that cyber threats have a complexity that cannot be addressed by existing security measures, which requires financial institutions to adopt more effective defense measures. Literature [30] found that due to the interconnectedness of the financial sector and the promotion of coordinated regulation, a more unified standard for cybersecurity is gradually being developed globally, and even though there are still differences in aspects such as data protection, combating cyberthreats requires international cooperation and information sharing. Literature [4] emphasizes that any damage caused to a bank has the potential to affect the entire economic landscape, so the management of cyber threats becomes very important. The financial threats faced by banks and other financial institutions are analyzed and the techniques as well as strategies to counter the threats are discussed. Literature [5] illustrates that the continuous development of banks in the digital era highlights the importance of cyber security measures. The aim of the study is to provide feasible recommendations for cybersecurity risks in banks to cope with the complex digital risks faced by banks and thus ensure the security of the financial sector.
Everything has two sides, the Internet in equality, efficiency, transparency and other advantages of the other side, is the emergence of endless information security problems, let alone will become a potential network security threats. This paper starts from the principle of financial institutions network information transmission security prevention, through the financial institutions situational awareness platform for network security data processing, and combined with frequency domain analysis and distributed processing to obtain the characteristics of financial institutions network security threats. The BiGRU model is used to learn the local dependencies of cybersecurity threat feature data, and the long-distance dependencies in sequence data are captured by the Transformer model, so as to establish a cybersecurity threat identification model for financial institutions. Based on the consideration of SQL injection attack, the SQLIA defense system is constructed for defending financial institutions’ cybersecurity threats by combining with multivariate execution. An intelligent planning method for cybersecurity defense strategy is designed through the theory of finite rationality to obtain a defense strategy that better meets the cybersecurity threats of financial institutions, thus enhancing the defense capability of financial institutions against cybersecurity threats.
The attributes of financial products and services are particularly suitable for publicizing, promoting, selling and servicing through the Internet – this is one of the foundations on which the financial Internet and Internet finance industry have been able to gain rapid development in recent years. Both Internet finance and financial Internet are utilizing the advantages of Internet technology in the collection, storage and processing of information to improve the processing efficiency of financial big data, which can enhance the ability to identify cybersecurity threats, the ability to control risks and the level of pricing, as well as provide customers with more convenient and affordable services.
In the big data environment, due to the large amount of data in financial institutions, the scope of data transmission security prevention must be expanded in order to effectively prevent invasive behavior, and to resist invasive behavior by means of active prevention. Based on the distribution characteristics of the information nodes in the financial network, the prevention system is set up so that it covers each intrusion attack node. If the information in a node is found to be invaded and attacked, an alarm is immediately issued, thus providing active defense [15].
According to the characteristics of financial network data, construct a data intrusion attack antigen set (a collection of elements to resist intrusion attacks), labeling parameters such as protocol types, ports, and IP addresses. According to the different access behaviors, the user access behaviors are split into two subsets. One subset is used to store normal access behavior and the other subset is used to store abnormal access behavior. Affinity is used as a tool for active defense against intrusion and two cases are set, in case of this threshold value is 1, it is considered that active defense is possible and if this threshold value is 0, it is considered that intrusion behavior cannot be effectively prevented. The threshold model is as follows: \[\label{GrindEQ__1_} f_{match} \left(x,y\right)=\left\{\begin{array}{l} {1,\quad \left({f_{h\_ dis} \left(x,y\right)\mathord{\left/ {\vphantom {f_{h\_ dis} \left(x,y\right) l}} \right. } l} \right)\ge \theta }, \\ {0,\;\quad \text{otherwise}}, \end{array}\right. \tag{1}\] where \(f_{h\_ dis} \left(x,y\right)\) represents the clone (access behavior) affinity (an indicator reflecting the characteristics of the antibody, which in this paper refers to the ability to defend against invasive behavior), \(f_{match} \left(x,y\right)\) represents the monoclonal antibody affinity, and \(l\) represents the character string.
In order to effectively prevent invasive behavior, there must be enough antibodies, and when the number of antibodies reaches a certain value, it can provide a good defense effect. However, some of the antibodies in the prevention process will be affected by the environment and other factors, resulting in the death of the antibody, the number of changes and so on. The number of antibodies in the defense system has the characteristic of dynamic change, flowing in from one side and out from the other. The dynamic set of immature antibodies can be expressed as: \[\label{GrindEQ__2_} I\left(t+\Delta t\right)=I\left(t\right)+\Delta t-\left(\frac{\partial I_{mature} }{\partial x_{mature} } +\frac{\partial I_{dead} }{\partial x_{dead} } \Delta t\right), \tag{2}\] where \(\frac{\partial I_{matures} }{\partial x_{mature} }\) represents the inflow process and \(\frac{\partial I_{dead} }{\partial x_{dead} }\) represents the outflow process. The superposition of the number of antibodies of the two processes is the total number of antibodies in the current set. Eq. (2) is utilized to describe the number of data invasive behaviors in a given time domain range.
In the process of using antibodies to defend against invasive behaviors, the tolerance of antibodies is required to be high. By activating the memory antibody, the antibody is made to shift from immature to mature state to defend against the invasive behavior. In this case, the behavior is an active behavior, which actively defends against the invasive behavior within the threshold of activation. The formula for the transformation of antibody properties is as follows: \[\label{GrindEQ__3_} \frac{\partial M_{active} }{\partial X_{active} } \Delta t=\frac{\partial T_{active} }{\partial X_{active} } \Delta t , \tag{3}\] where \(M_{active}\) represents mature active antibody, in the activated state, \(T_{active}\) represents mature antibody, in the activated state, and \(X_{active}\) reaches the standard active antibody.
When an intrusion occurs in the network of the financial institution, the memory antibody is activated, causing the immature antibody to evolve to the mature antibody, which actively recognizes the intrusion and stops the access, protecting the information data in the transmission process, and playing a good preventive role.
For financial institution big data, this paper relies on the financial institutions’ situational awareness platform to collect financial massive data, and the data obtained from traffic logs, network devices and other dimensions are analyzed and processed in a complex manner with high real-time and high efficiency. The network security data processing flow of financial institutions is shown in Figure 1, which applies a large number of advanced cutting-edge technologies to support and realize data security analysis and processing capabilities. Among them, Flink is a distributed processing engine for streaming data and batch data, and data processing adopts Flink to process streaming data, adopts Ambari for management and deployment, is compatible with Flink eco-software, and supports computational models such as SQL, Table, CEP, and machine learning. The situational awareness of big data for financial institutions is based on Apache Flink, a distributed data stream processing system, and Siddhi, a complex event computing engine, with excellent characteristics of high throughput, low latency, high performance and high flexibility.
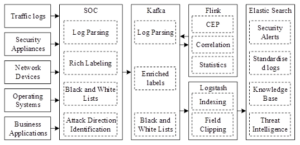
The situational awareness data processing of financial institutions’ big data contains various big data-related technologies, which can be configured through security analysis based on the business scenario’s statistical model, rule model, correlation model, etc., and perform the calculation of statistics, summation, mean value, unique value and other operators on any field in the data. It can realize high real-time computing of network security in financial service scenarios through the association of event priority and field containment relationship for multi-source data.
On the basis of constructing the data processing flow of financial network security information transmission, the threat features of financial institutions’ network transmission security are extracted. Combined with the network topology restructuring method to realize the distributed reconstruction of the dynamic features of network transmission information, the dynamic iterative processing of network information transmission is realized according to the combined frequency domain factor distributed fusion technology. This technique combines the combined frequency domain analysis method with distributed processing, analyzes the frequency domain data collected by each node in the network, extracts the frequency domain factors related to network transmission, and passes the analyzed frequency domain factor information to other nodes in the network [26]. Distributed computing and communication are used to realize information exchange and sharing, and dynamic iteration is carried out between nodes to optimize and improve network information transmission by gradually adjusting and optimizing network transmission parameters and strategies through continuous information exchange and updating. The set of principal component feature distribution of all network transmission channels of a particular LAN is obtained as: \[\label{GrindEQ__4_} \begin{array}{l} {\min \frac{1}{2} \left\| W\right\| +C\sum\limits_{j=1}^{t}x (t)\xi _{j} }, \;\; \text{such that}\;\;{y_{j} \left(W\cdot x\left(t\right)+b\left(x\right)\right)+\xi _{j} \ge 1}\;\; {\xi _{j} \ge 0,j=1,2,\cdots ,l}, \end{array} \tag{4}\] where, \(W\) is the node weight, \(C\) is the suspected attack behavior capacity parameter, \(\xi _{j}\) is the base learner for the \(j\)th round of training, each individual learner is independent of each other, and the data collection is performed using self-sampling method in the original training set. The speed of each individual learning in the original training set is \(V^{i} =\left(v_{i1} ,v_{i2} ,\cdots ,v_{iD} \right)^{T}\) and the location of the network threat point is \(X_{i} =\left(x_{i1} ,x_{i2} ,\cdots ,x_{iD} \right)^{T}\). Threat dynamic parameter analysis is carried out in the original training set using self-service sampling method, and the distribution kernel function of the base learning for the \(j\)th round of training is \(k\left(x_{i} ,x_{j} \right)\). Individual base learners are independent of each other and multiple primary individual learning models are obtained as: \[\label{GrindEQ__5_} \begin{array}{l} {\min _{\alpha } \frac{1}{2} \sum\limits_{i=1}^{l}\sum\limits_{j=1}^{l}y_{i} y_{j} \alpha _{i} \alpha _{j} K\left(x_{i} ,x_{j} \right)-\sum\limits_{j=1}^{l}\alpha _{j} }, \;\;\text{such that}\;\; {\sum\limits_{j=1}^{l}y_{j} \alpha _{j} =0}\;\; {0\le \alpha _{j} \le u\left(x_{j} \right)C,j=1,2,\cdots ,l}, \end{array} \tag{5}\] where, \(K\left(x_{i} ,x_{j} \right)\) is the training kernel function of real attack samples, \(\alpha _{i}\) is the proportion of real attack samples in the dataset that are recognized, \(\alpha _{j}\) is the proportion of real attack samples in the dataset that are not recognized. \(y_{i}\) is the proportion of real attack samples in the dataset that are recognized, \(y_{j}\) is the proportion of real attack samples in the dataset that are not recognized, and \(u\left(x_{j} \right)\) is the feature parameter of the \(j\)th round of training.
Using the greedy algorithm of fuzzy clustering, the subscript of security threat identification is obtained \(g_{best}\). Judging by the threshold, but less than the threshold indicates the existence of the possibility of attack, at this time, the objective function containing the regular term is obtained as: \[\label{GrindEQ__6_} w_{ij} =\beta w\left(e_{p} k_{q} \right)+K\left(x_{i} ,x_{j} \right),\beta >1 , \tag{6}\] where \(\beta\) is the adaptive weighting coefficient of sample \(x\) on the decision tree, and \(w\left(e_{p} k_{q} \right)\) denotes the objective function gain, whereby all the values of each feature are traversed through the time gain judgment to obtain the threat characteristics of the network transmission information as: \[\label{GrindEQ__7_} Y_{k} =w_{ij} \left[y_{k1} ,y_{k2} ,\cdots ,y_{kj} ,\cdots ,y_{kj} \right],k=1,2,\cdots ,N , \tag{7}\] where \(y_{kj}\) denotes the set of gradient instance data, and \(N\) is the data length, from which the feature extraction model is established, and the dynamic detection of network information security threats is carried out based on the feature extraction results.
In the new era, the development of technology has brought great influence to the development of financial institutions, and the huge amount of data it generates makes financial institutions pay more and more attention to network security threats, and the application of technology can effectively realize the dynamic identification of network security threats. However, through the analysis of the actual situation, it is found that there are many problems in the identification of network security threats, and the application of technology should be combined with the computer network to avoid network security problems affecting the application and development of technology. Therefore, financial institutions need to deeply explore the threat characteristics of financial data in network transmission, combined with the actual situation of technology application, in order to improve the level of financial institutions services and network security.
The overall structure and flow of the financial network security threat recognition model is shown in Figure 2. The design idea of the model proposed in this paper lies in the advantages of financial cybersecurity threat feature selection and data balancing processing, which in turn improves the model’s ability to process complex sequence data through the deep integration of Transformer and BiGRU. Compared with existing research, this model has significant differences and advantages in feature optimization, data balancing, and long dependency capturing.
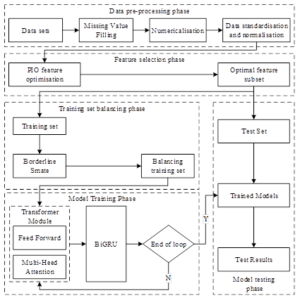
In this paper, we adopt the combined architecture of Transformer + BiGRU, in which Transformer is responsible for capturing long-distance dependencies in sequence data, while BiGRU focuses on learning local dependencies in data and controlling the flow of information through a gating mechanism, so that the model can be more flexible to adapt to different levels of feature representation. This structural design makes the model more accurate and efficient in handling data with complex patterns. The final results are obtained by performing performance tests on the previously trained model using a prepared test set after model training.
The model in this paper has excellent processing capabilities, especially on high dimensional and long sequence data, and achieves high prediction accuracy and efficiency through feature optimization, data balancing and deep neural network integration. Its hybrid architecture strategy not only enhances the flexibility and robustness of the model, but also effectively prevents the overfitting problem and improves the practicality and scalability of the model.
BiGRU is a structure that uses two unidirectional gated recurrent units.The basic idea of this structure is to process the input sequence in both forward and backward directions at the same time and connect the outputs from both directions to a common output layer.Conventional recurrent neural networks can only utilize the past input information when making predictions.BiGRU will process the input sequence simultaneously in both forward and backward direction of the GRUs for processing. In this case, the forward GRU processes the input sequence in normal chronological order, while the backward GRU processes the input sequence in reverse order. In this way, the hidden state at each moment captures both past and future contextual information [12]. The computational procedure of BiGRU neural network is as follows:
Assuming that the input at time step \(t\) is \(x_{i}\), the activation function of the hidden layer is \(\partial\), and that the left side of Eq. are the forward and backward hidden states, respectively, then: \[\label{GrindEQ__8_} \overrightarrow{h_{t} }=\partial \left(x_{t} W_{fx} +{\mathop{\to }\limits_{h_{t-1} }} W_{fh} +b_{fh} \right) , \tag{8}\] \[\label{GrindEQ__9_} {\mathop{\leftarrow }\limits_{h_{t} }} =\partial \left(x_{t} W_{bx} +{\mathop{\to }\limits_{h_{t-1} }} W_{bh} +b_{bh} \right) , \tag{9}\] where \(W_{fx}\), \(W_{fh}\), \(W_{bx}\), \(W_{bh}\) denote the weight parameters, \(b_{fh}\), \(b_{bh}\) denote the bias corresponding to the forward hidden state and backward hidden state, respectively. From this, the output \(GRU\_ O_{t}\) of the output layer is calculated as: \[\label{GrindEQ__10_} GRU\_ O_{t} =\left({\mathop{\to }\limits_{h_{t} }} \left|{\mathop{\leftarrow }\limits_{h_{t} }} \right. \right)\cdot W_{q} +b_{q} . \tag{10}\]
The final output is calculated by weighted splicing of forward hidden state and backward hidden state, which can learn the effective information and also keep the output dimension unchanged, which reduces the dimension and helps to reduce the training time compared to directly splicing the hidden state in both directions.
The Transformer model is based on the “encoding-decoding” framework, where the input is word vectors and positional encoding is added after each word vector to prevent semantic confusion [13]. The positional coding is calculated as follows: \[\label{GrindEQ__11_} PE(pos,2i)=\sin \left(\frac{pos}{10000^{\frac{2i}{dmodel} } } \right) , \tag{11}\] \[\label{GrindEQ__12_} PE(pos,2i+1)=\cos \left(\frac{pos}{10000^{\frac{2i}{dmodel} } } \right) , \tag{12}\] where \(pos\) denotes the absolute position of the word in the sentence and \(dmodel\) denotes the dimension of the word vector.
Transformer uses the Multi-Head Attention mechanism, which provides multiple “representation subspaces”, allowing the model to attend to information from different “representation subspaces” at different positions, i.e., the model can capture richer feature information through “Multi-Head”, the model can capture richer feature information. The Multi-Head attention mechanism is diagrammed and described as: \[\label{GrindEQ__13_} MultiHead(Q,K,V)=Concat(head_{1} ,…,head_{h} )W^{0} , \tag{13}\] \[\label{GrindEQ__14_} head_{i} =ATT(QW_{i}^{Q} ,KW_{i}^{K} ,VK_{i}^{V} ) , \tag{14}\] where \(Q\) denotes the query vector, \(K\) denotes the key vector, \(V\) denotes the value vector and \(WQ,WK,WV\) is the weight.
A residual connection layer is added to each sublayer in the Transformer language model to avoid gradient vanishing. In order to speed up the training of the model and improve the stability of training the input data is normalized and the normalization layer uses the LN algorithm. In the Transformer model, each word vector is computed by the multi-head attention mechanism and then further processed by the feed-forward network to extract richer semantic information.
In order to verify the effectiveness of the cybersecurity threat recognition model for financial institution big data designed in this paper, a comparison experiment is set up in this section. The training cluster used is the UNSW_NB dataset with intrusion signals in financial institution big data, and several different algorithms are selected as comparisons, with the evaluation indexes of accuracy rate, precision rate, recall rate and F1 comprehensive score. The cyber security threat recognition results of different models are shown in Table 1.
The accuracy, precision and recall of the model proposed in this paper reached 90.64%, 90.51% and 89.84%, respectively, and the F1 score reached 90.78%, which achieved relatively good results in all the evaluation indexes. This is because traditional machine learning methods are easily affected by irrelevant and redundant features, so the performance of the model is still not as good as the deep learning model. In this paper, the model learns features through neural networks, combines low-level features to form a more abstract and nonlinear high-level representation, and then utilizes the input-output relationship between the data to effectively improve the accuracy of cybersecurity intrusion detection of financial institutions’ big data, and combines the BiGRU and Transformer models, which can better mine the security threat features in financial institutions’ big data. Compared with the existing VAE-CWGAN, MCNN-DFS, GAN-BiLSTM, SSAE-LSTM, CNN-GRU, and CNN-BiLSTM models, the BiGRU network in this paper’s model fully combines the advantages of the GRU network, improves the problem of the gradient vanishing, and constructs a deeper network structure, extracts more complex and abstract features. Subsequently, the Transformer model is utilized to improve the feature learning ability of cyber security threats, thus solving the problem of insufficient feature extraction ability of the model. The method in this paper has great improvement for the aspects of high dimensionality of features, imbalance of dataset and single model, and has higher accuracy in identifying few attack traffic in financial institutions’ networks, and these good experimental results further prove the effectiveness of this paper’s model.
| Model | Accuracy | Precision | Recall | F1-score |
| RF | 78.97 | 75.04 | 81.15 | 79.42 |
| SVM | 78.35 | 75.72 | 78.87 | 73.51 |
| KNN | 80.51 | 77.63 | 77.65 | 77.84 |
| VAE-CWGAN | 89.03 | 88.51 | 88.57 | 88.38 |
| MCNN-DFS | 82.87 | 81.42 | 81.02 | 81.42 |
| GAN-BiLSTM | 89.25 | 85.79 | 85.72 | 85.51 |
| SSAE-LSTM | 87.66 | 83.75 | 71.98 | 82.97 |
| CNN-GRU | 83.08 | 8563 | 86.18 | 83.48 |
| CNN-BiLSTM | 88.03 | 85.72 | 84.75 | 85.92 |
| Ours model | 90.64 | 90.51 | 89.84 | 90.78 |
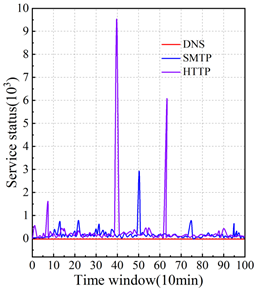
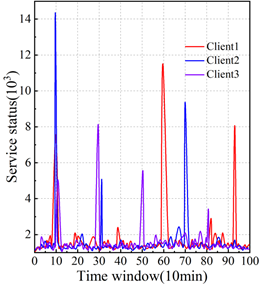
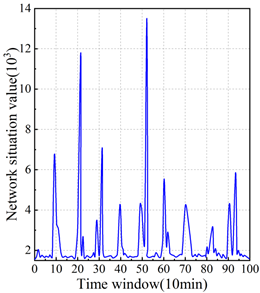
The network security posture analysis of financial institutions takes the attack as the starting point, selects 10 minutes as a time window, and calculates the security posture change values of different services, different hosts, and networks in a hierarchical manner, reflecting the occurrence of network attacks in the time window by analyzing the sudden change of the security posture values in each time window. Three hosts with IPs 192.168.126.12, 192.168.126.14, and 192.168.126.16 are selected as the research objects, which are named Client1\(\mathrm{\sim}\)Client 3 respectively, and the network security posture of the three hosts is analyzed. Figure 3 shows the results of network security posture analysis, in which Figure 3(a) shows the posture graphs of the three services of DNS, HTTP and SMTP in Client1, and Figure 3(b) and (c) show the posture changes in the host layer and network layer, respectively.
In the security posture results of the service layer, the host has high service posture values for HTTP service in the 38th-42nd time windows as well as in the 60th-65th time windows, and has been subjected to a single large-scale and larger-scale attack, which requires the financial institution to pay special attention to it. The SMTP service was attacked once on a small scale in the time window 49-51, in addition to which the HTTP and SMTP services were attacked several times on a smaller scale. Financial institutions need to make appropriate protective measures based on the network security posture of financial services.
In the results of the security posture at the host layer, Client1 suffered a small-scale attack in the 10th time window, a larger-scale attack in the 59th to 62nd and 93rd to 95th time windows, and many times suffered from small-scale attacks; Client2 suffered a large-scale attack in the 10th and 71st to 75th time windows, a large-scale attack in the 31st to 33rd time windows, and many times suffered from small-scale attacks. \(\mathrm{\sim}\)Client3 suffered one large-scale attack in the 10th-13th, 28th-32nd, and 48th-52nd time windows, and many minor attacks in the rest of the time. Based on the results of the cybersecurity posture of financial hosts, skill organizations need to pay more attention to hosts with high attack threat indexes.
In the security posture results of the network layer, the network suffered a large-scale attack in the 20th to 22nd and 52nd time windows, and suffered large-scale attacks and small-scale attacks several times. This figure can reflect the security status of the network correctly and help financial institutions to monitor the security status of the network. Financial institutions should survey and protect the network according to the posture figure, and pay attention to the information of users who accessed the network in the 20th-22nd and 52nd time windows, so as to confirm the malicious access users and take appropriate measures in this regard.
In the context of the development of the era of big data, computer network technology has been widely used in the financial field, so the network security and stability of financial institutions has put forward higher development requirements. As an important carrier of information technology and network technology, computer network carries the security defense of the entire financial network, and once the network is maliciously attacked, individuals and other private data information will be seriously affected, and even endanger the safety of life. Deep learning technology as an intelligent emerging technology, has a strong robustness and stability, its application to the network security defense of financial institutions, can effectively improve the overall security performance of the network, to avoid malicious attacks on the network.
Most of the multi-variant execution architectures use Leader-Follower or Master-Slave design, for the system calls that are not voted, the monitor assigns them to the Leader/Master variant for execution, and then synchronizes the results to the Follower/Slave variant, this approach can effectively reduce the false positives, but it increases the security threats [31]. Once the Leader/Master variants are controlled, the defense effectiveness of the multivariate execution architecture will be greatly reduced. In this paper, we propose the SQLMVED network security defense architecture based on multivariate execution as shown in Figure 4. To avoid the security threat of Leader-Follower/Master-Slave mode, synchronous mode is used, and the system consists of a user request agent, a multivariate responsible for processing the request, a database agent, and a database.
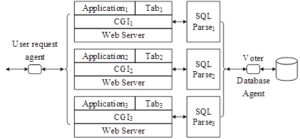
The user request agent is the gateway to the web service, when it receives a request initiated by the user, it makes three copies of the request and forwards them to the multivariate. When it receives a response from a multi-variant, it votes on it, and if there is a unanimous majority response, it returns it to the user, otherwise it rejects the response. The user request broker is based on the Nginx implementation, which realizes the forwarding of the same user’s request to multiple variants and the voting of the same user’s response. The multi-variants consist of a web server, a CGI, and a deployed application, where the application uses a randomization method to randomize changes to the SQL, and the labels used are different between the variants. The database agent consists of a SQL syntax parser, SQLParse, which serves each variant independently, and a voting agent that compares the results of its parsing.The SQL syntax parser is based on the sqlparse/keywords.py file, which aligns the tokens.Keyword with the randomization labels, and completes the process of parsing the randomized SQL and de-randomizing it.
Intelligent planning aims to achieve desired goals by executing a series of actions. By using it in the cyber security defense scenario of financial institutions, it can simulate the human defense behavior, focus on the current urgent defense measures of the system, and reach the target state by executing a series of defense strategies from the initial state, so as to achieve the cyber security defense goal.
In this paper, considering the advantages of the finite rationality method in supporting the selection of cyber defense strategies for financial institutions, we set the boundary conditions of time, cognition and information, expand the STRIPS language finite rationality to STRIPS-BR, intelligently allocate resources within the scope of finite rationality, plan the best current cybersecurity defense scheme and automate its implementation, so as to realize the asset security goal.
STRIPS-BR first defines three constraints in finite rationality, i.e., time-limited, cognitively limited, and information-limited. Among them, time-limited \(BR-A\left(T\right)\) and cognitively limited \(BR-A\left(C\right)\) can be judged by checking whether the time count and cognitive depth of the state have exceeded their respective limits, respectively, and information-limited \(BR-A\left(I\right)\) includes unknown or incorrectly assumed asset states \(S-BR\), goal propositions \(G-BR\), and available finite defense strategies CM-BR. Based on this information, we build a search tree to obtain all the planning scenarios that can satisfy the goal state \(P^{x}\). The defense strategy in \(P^{x}\) Sequential execution results in \(O^{x}\) and \(rank\left(s_{i} \right)\) is the actual sequence of defense strategies executed.
To determine the optimal (highest utility) defense planning scheme, define \(U\left(P_{0,k}^{x} \right)\) as the cumulative planning utility of the defense strategies from the beginning to the \(k\)th defense strategy in planning \(P^{x}\), i.e: \[\label{GrindEQ__15_} U\left(P_{0,k}^{x} \right)=\sum\limits_{t=0}^{k}w_{t}^{x} , \tag{15}\] where \(w_{k}^{x}\) is the weight of the \(k\)rd defense strategy \(cm_{k}^{x}\) in \(P^{x}\), i.e: \[\label{GrindEQ__16_} w_{k}^{x} =in-\deg ree+0.1\sum\limits_{v}c vss_{v} +\lambda , \tag{16}\] \[\label{GrindEQ__17_} cvss_{v} =\alpha CVSS_{v} , \tag{17}\] where in-degree is the in-degree of defense strategy \(cm_{k}^{x}\), \(cvss_{v}\) is the product of the probability \(\alpha\) of adopting defense strategy \(cm_{k}^{x}\) against vulnerability \(v\) and the CVSS score of vulnerability \(v\), and \(\sum\limits_{v}cvss_{v}\) is the sum of the \(cvss_{v}\) values of the existing vulnerabilities \(v\) that can be solved by executing the defense strategy \(cm_{k}^{x}\) reflecting the importance of the strategy for the existing vulnerabilities. \(\lambda\) is a correlation factor representing the correlation between the current defense strategy \(cm_{k}^{x}\) and the previous one, \(\lambda =0.3\) if the current defense strategy is related to the previous one (belonging to the same security means), and \(\lambda =0\) otherwise.
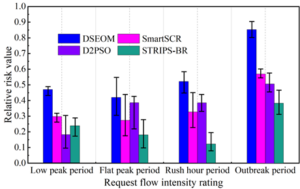
In this paper, the request traffic transmitted by financial institutions is divided into four different request traffic intensity levels: the “low peak period” from 0:00 to 5:00, the “peak period” from 6:00 to 11:00, the “peak period” from 12:00 to 17:00, and the “burst period” from 18:00 to 23:00. This paper proposes a SQLIA defense system based on multi-variant execution, and uses the STRIPS-BR defense strategy to defend against network security threats in financial institutions. In order to measure the defense effect of the STRIPS-BR strategy on the financial service system, the relative risk value of the successful attack of the system when the financial service system adopts different defense strategies for system dynamic configuration is shown, as shown in Figure 5.
Comparison of the results shows that STRIPS-BR reduces the system risk value relative to other strategies by 22.68%, 48.57%, 74.81% and 41.54% on average during the low-peak, flat-peak, peak and outbreak periods, respectively, which indicates that STRIPS-BR has a stronger financial services network security defense capability. With the arrival of the traffic outbreak period, the advantage of STRIPS-BR is more obvious, which shows that the STRIPS-BR defense policy for financial services network resource allocation and defense configuration intelligent planning for integrated decision-making can better respond to the changes in the request traffic. financial services under the DSEOM policy has the largest system risk value, which is mainly due to the fact that the DSEOM targets critical financial services for The main reason is that DSEOM protects against critical financial services, and there is a possibility that attackers bypass critical financial services to intrude into critical data nodes, so the financial service system risk assessment under this strategy has a poor performance.The SmartSCR strategy has a significant security improvement compared to the DSEOM strategy, because the SmartSCR strategy improves the security of the financial service system by providing protection for all financial services. The reason for the better defense effect of STRIPS-BR is that it takes into account the security gain of the financial service system by the randomization of replicas introduced in the resource allocation process, so that the security of the financial service system can be further strengthened by the targeted resource allocation under the dynamic user traffic.
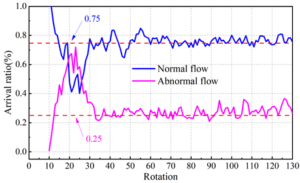
Based on the SQLIA defense system executed by multi-variants, combined with the results of network security threat identification, a network security defense strategy based on STRIPS-BR is designed. In order to further verify the effectiveness of the strategy’s network security threat defense, this paper takes the proportion of passage through normal traffic (PA) and the proportion of passage through malicious traffic (PB) as the evaluation indexes, and obtains the results of the effectiveness of the financial institution’s network security threat defense as shown in Figure 6.
As can be seen from the figure, after 10 rounds, the proportion of attack traffic reaching the target host is stabilized at 25%, and the proportion of legitimate traffic reaching the target host is maintained at about 75%, which indicates that the financial institution network security defense strategy based on STRIPS-BR plays an obvious mitigation effect on flooding attack traffic, and it can compress the passage rate of malicious traffic as much as possible, while reducing the impact on legitimate traffic to ensure that the network bandwidth resources are not occupied by malicious traffic.
Under the environment of unpredictable cyber shock, cyber security has been the focus of extensive attention from both theoretical and practical circles in recent years. And finance, as the weathervane of a country’s economy, is the industry most vulnerable to cyber siege. Whether it is risk management, bookkeeping and clearing, or asset pricing and digital currency, the financial industry’s network construction has been in the forefront of all industries. Under the existing big data environment of financial institutions, it is crucial to ensure the secure transmission of financial institutions’ networks and improve their ability to identify and defend against cybersecurity threats.
The asset security operation and maintenance platform is used to clarify the asset base, form the network and air topography, and establish a unified security patch and unified security policy distribution and adjustment system to realize effective asset security reinforcement. Through effective data collection and intelligence production on the endpoint side, network side and analysis side, we build a situational awareness platform system and conduct data aggregation and analysis to form effective security policies.
Financial institutions must face up to the security challenges brought about by open scenarios and the growth in the scale of information systems, comprehensively improve network security planning capabilities, and implement full life cycle security planning, construction, operation and maintenance. Important information assets and large-scale information assets need to be set up with the objective enemy situation of “the enemy is already inside and the enemy will be inside”. With reference to the “threat framework”, we should update our systematic knowledge of threat actors and attack activities, so as to deepen and improve the setting of the hostile situation and thus improve defense.
With escalating cyber threats and increased regulatory demands, it is imperative for financial institutions to establish a comprehensive cyber security response strategy to protect their systems and entrusted data from cyber attackers.
Establish a reliable access management strategy. Key components of an access management strategy include cloud access security agents, multiple authentication, privileged access management, and zero-trust network access. Cloud access security proxy solutions monitor and manage access to an organization’s cloud-based applications, and multiple authentication requires users to authenticate to an account using a combination of multiple factors, such as passwords and physical tokens. Privileged access management solutions are critical for accounts with higher access rights to monitor and manage sensitive systems and data, and zero-trust network access can enable financial institutions to manage data security risks and meet regulatory compliance requirements by providing access to data.
Ensure endpoint security and user safety and trust. One is Extended Detection and Response, a solution designed to take a more holistic approach to detecting and remediating threats by collecting data from multiple sources (endpoints, email, network traffic, etc.) and analyzing it to identify these attacks. The second is the Secure Web Gateway, which sits between users and the Internet and proxies all connections, enabling organizations to block access to inappropriate or dangerous sites and monitor for malicious content.
The article uses frequency domain analysis and distributed processing to extract the cyber threat features of financial institutions, establishes a cyber security threat identification model by combining BiGRU and Transformer model, then establishes a SQLIA defense system based on multi-variant execution, and designs a STRIPS-BR strategy for cyber security threat defense of financial institutions. The comprehensive score of F1 for cybersecurity threat identification of financial institutions based on BiGRU and Transformer model can reach 90.78%, which can effectively analyze the cybersecurity posture of financial institutions under different network layers. The relative risk value obtained by the STRIPS-BR strategy based on intelligent planning of cybersecurity defense strategies is 41.54% lower than that of other strategies during the outbreak period, which can suppress the abnormal traffic of the financial network at about 25%. Financial institutions need to establish a network security threat and defense system, which is carried out in the dimensions of access management policy, endpoint security and user security, so as to ensure the improvement of the security level of financial institutions’ services.